-
Follow up to Setting up SSL Certs for IIS 10
As a follow up to this article from the past, I got email from a reader who gave a link to a useful SSL Checker.
[visual-link-preview encoded=”eyJ0eXBlIjoiZXh0ZXJuYWwiLCJwb3N0IjowLCJwb3N0X2xhYmVsIjoiIiwidXJsIjoiaHR0cHM6Ly93d3cud2Vic2l0ZXBsYW5ldC5jb20vd2VidG9vbHMvc3NsLWNoZWNrZXIvIiwiaW1hZ2VfaWQiOi0xLCJpbWFnZV91cmwiOiJodHRwczovL2R0MnNkZjBkYjh6b2IuY2xvdWRmcm9udC5uZXQvd3AtY29udGVudC90aGVtZXMvd2Vic2l0ZXBsYW5ldC9pbWcvd2Vic2l0ZXBsYW5ldF9pbWFnZS5wbmciLCJ0aXRsZSI6IkZyZWUgU1NMIENoZWNrZXItT25saW5lIFdlYnNpdGUgQ2VydGlmaWNhdGUgQ2hlY2tlciBUb29sIiwic3VtbWFyeSI6Ikp1c3QgZW50ZXIgeW91ciBVUkwgaW50byB0aGlzIGZyZWUgdG9vbCBhbmQgcXVpY2tseSBkZXRlY3QgYW55IGlzc3VlcyB3aXRoIHlvdXIgU1NMIGNlcnRpZmljYXRlIGluc3RhbGxhdGlvbi4gR2V0IHRoZSBmdWxsIGFuYWx5c2lzIGFuZCBleHBpcmF0aW9uIGRhdGUuIiwidGVtcGxhdGUiOiJ1c2VfZGVmYXVsdF9mcm9tX3NldHRpbmdzIn0=”]
I’ve have used this site (and others) to inspect my SSL deployments. This is handy tool to add to your collection.
Thanks for the tip Lisa!
~ScottGeek
-
App Registration Link
This seems to want to move me off to Azure…
But for now the link still works…
https://apps.dev.microsoft.com
-
AS2 and the Mysterious Certificate
Before the knowledge gets left somewhere forgotten…
You will need makecert.exe (and place on a dev or tst where you can generate a cert with a private key) **The matter to remember here is that we will be using the logged user’s private Certificate store to actually generate the private key file.
So the mysterious Makecert:
makecert -r -pe -n “CN=<Your CN name or a full CN set of values>”
-b 07/13/2018 -e 07/13/2023 -len 2048 -eku 1.3.6.1.5.5.7.3.1
-ss my “<Name of CER file>.cer” -sr currentuser -sky exchange
-sp “Microsoft Enhanced RSA and AES Cryptographic Provider” -sy 24 -a “sha256” -nscp
The important parts:
-n ‘CN=<NAME THAT CERT>”
-b and -e are the start and expire dates
-len 2028 1 KB multiples of how long the key needs to be (not what type of key i.e. sha256, 512, etc)
-ss my “<Name of the cer file>” This is the actual cer file to share with the external- is has the public key. Do not share files with private keys!
When you execute this Markcert – you will get a <Name of cer file> in the local directory. (don’t panic, we’re not finished).
Next we run the mmc.exe:
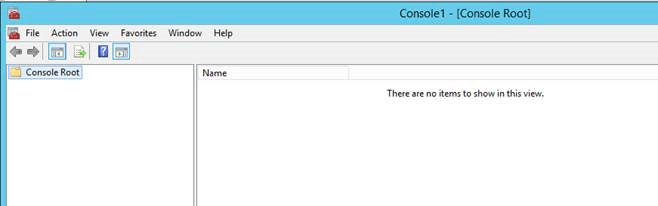
This is the opening window for MMC.exe Add/Remove Snap-in… (unless you saved a console, then just open it)
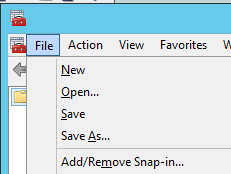
MMC – File -> Add/Remove Snap-in Add Certificates and select “My user account”:
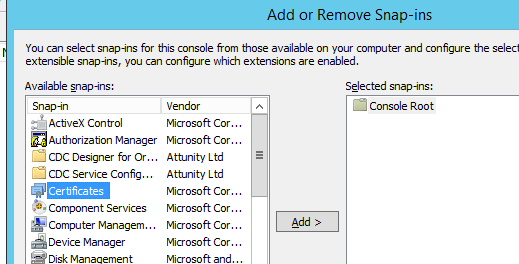
Select Certificates in the list. 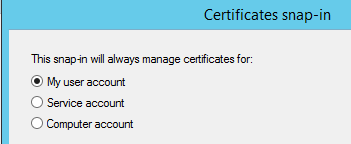
Make sure that “My user account” is selected as the certificate location. “Finish” and “OK”
Look in the Personal/Certificates (note the name is the CN=value)
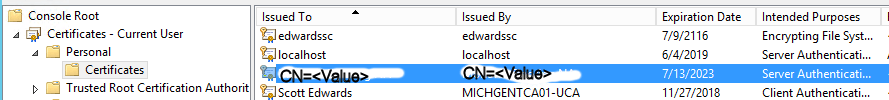
That’s the Server cert we just created… next we need to export to a Private PFX…
Right-Click cert… All Tasks… Export.
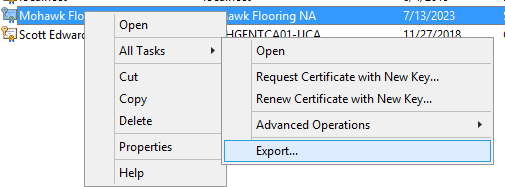
Make sure you select Yes, export the private key:
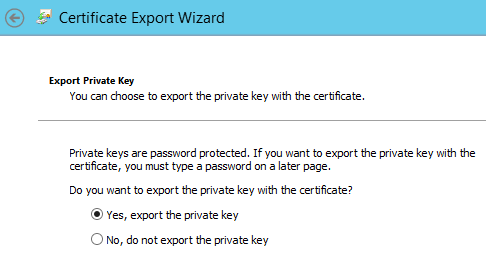
Next
Must have a password:
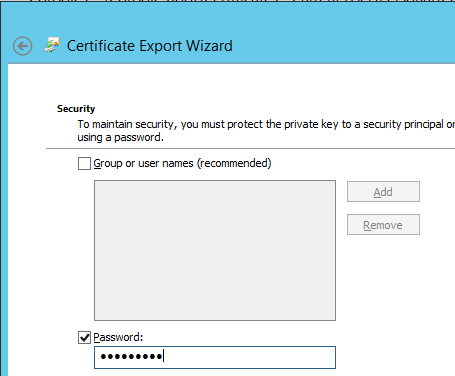
Next… pick a name for the pfx file
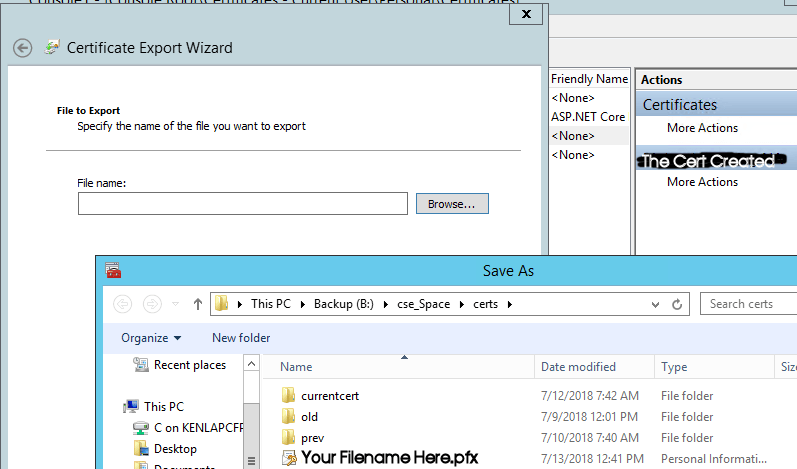
Next… Finish:
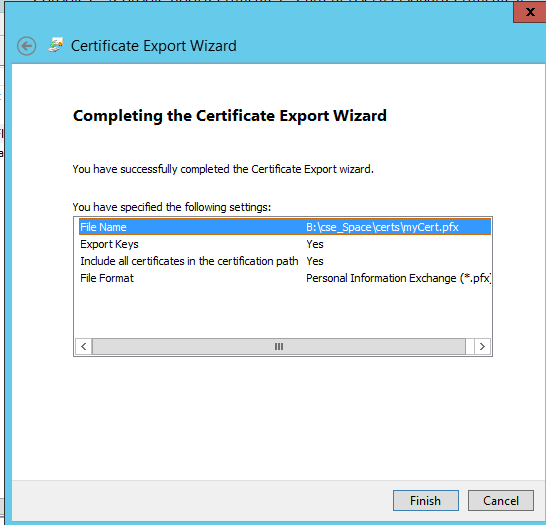
Now you have the two cert files:
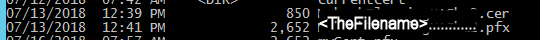
The cer file is what is shared with externals. NEVER Share your pfx (private key file) and password with external folks!!
The pfx file is what you need to add to the Cert stores on your server than needs to encrypt or decrypt files
When importing the PFX make sure you select Personal Information Exchange and Not the cer file:
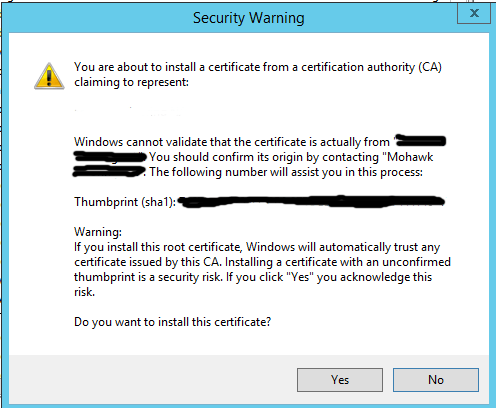
A new cert going into the Trusted Root Cert Authority will get this warning. This just means that you are about to trust the cert you just created. That’s normal for a seft-signed cert…
This is what a good cert should looks like:
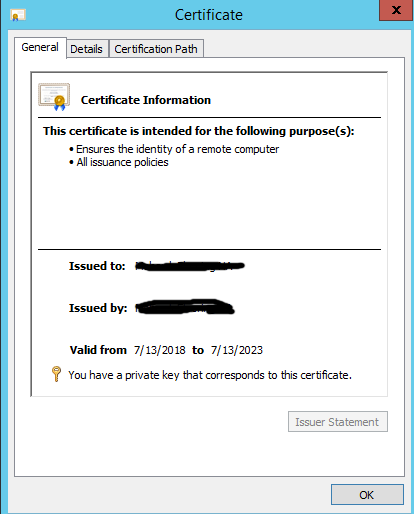
Now for BizTalk AS2 to use these new Certs, you must install them in the
- Trusted Root Certification Authorities (this insures that the self-signed is trusted)
- Other People (this is where the Sent Port Certificate browse with look)
- Personal (this is imported that you use the AS2 Host ISO user account! Otherwise you will get a AS2 error about the cert cannot be found)
I think that the most of it…
~ScottGeek
-
Setting up SSL Certs for IIS 10
So as I enter the world of suffering to get SSL working on some sites… I noticed that most SSL providers (at least the free one I’ve been using) – don’t provide the cert in the file format I need to do just a “import” within IIS. Go figure!
So what to do?
Well as it turns out there’s a utility to make the the crt formatted file into a pfx (which is what IIS likes).
openssl – look for it on the inter-tubes
openssl pkcs12 -export -out anotherCert.pfx -inkey private.key -in certificate.crt
Another point… I generally use SSL For Free for creating quick free SSL certs- they only last 90 days, but if you want longer lasting Certs… yeap you have to pay for them.
And finally, hosting multiple sites on a single IP and IIS server, one does need to get specific site SSL certs. The thing to remember to so make sure you select the “Require Server Name” check box as on, in the Bindings config. Otherwise you will get an error when selecting a site SSL cert. The warning message will say something to the effect of the cert being set for all sites being hosted. Ya that’s not what you want of course, as a cert for Site.Name.Domain will get assigned to all the sites being hosted. It’s a simple check box to miss, but it’s important.
